Emerald Blockchain Course class 10 the PoW security model in the physical and social layers.
You can watch this class here:
In the following sections we will explain the physical and social layers of the security model of proof of work blockchains. We will also explain the real security and risks, and the difference between the "trustless" and "trust minimization" concepts.
1. Physical layer security (proof of work) and social layer security (the coordination problem).
As we explained in our previous classes about Bitcoin and proof of work, Nakamoto Consensus has very strong security and monetary guarantees. Below is the general model of how proof of work incentivizes the ecosystem to reinforce the safety of the network.
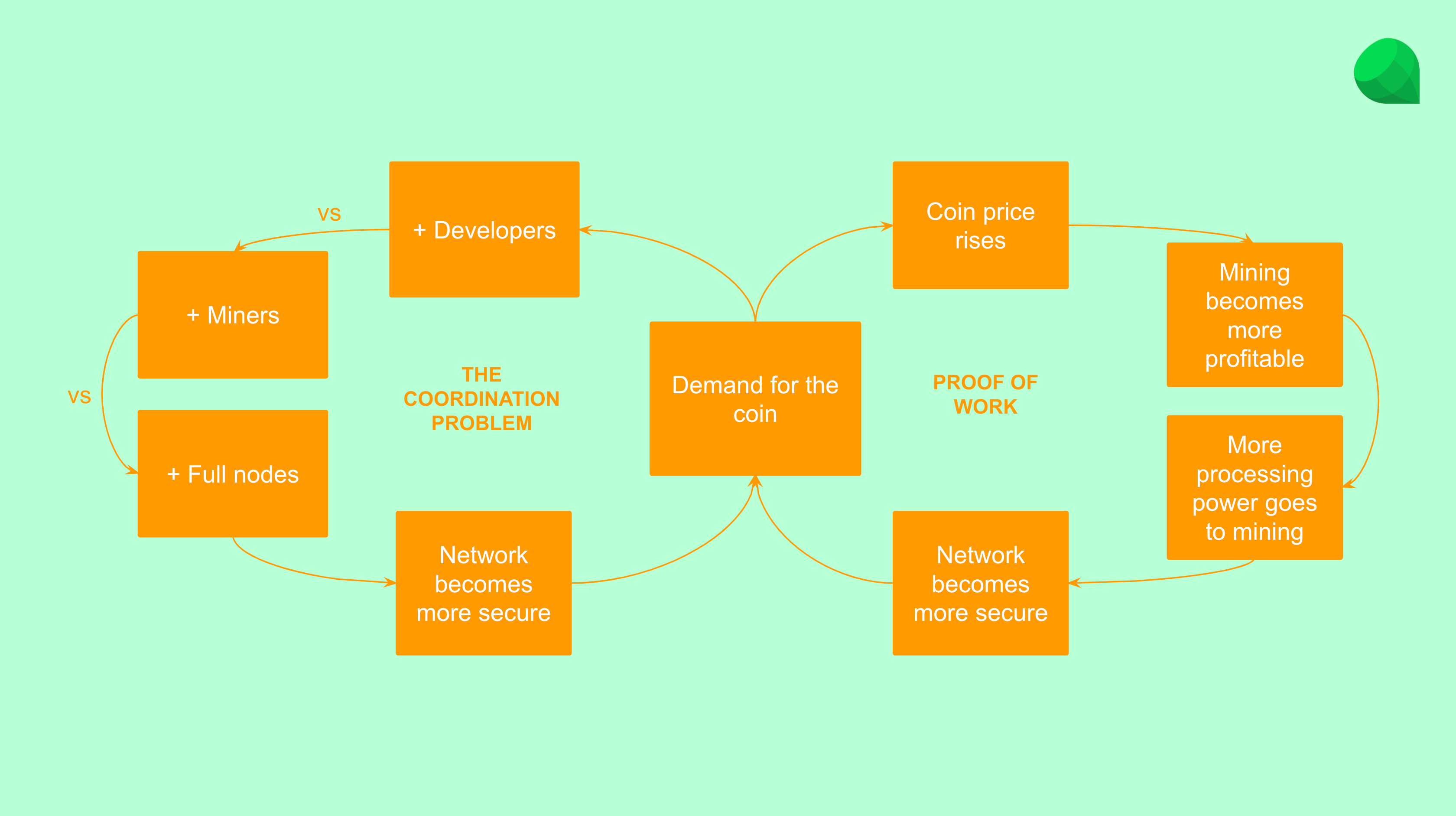
As seen in the diagram above, there are two virtuous circles that reinforce each other as the network grows.
1.1. Proof of work at the physical layer.
It all starts with demand for the native coin of the blockchain. When there is more demand, the price rises, and when the price rises mining becomes more profitable incentivizing miners to increase their computing power directed at creating blocks with stronger cryptographic stamps or hashes.
As the stronger cryptographic stamps or hashes make the network more secure, and the cryptocurrency sounder, this makes the coin more attractive increasing its demand, therefore reinforcing the physical layer's safety.
1.2. The coordination problem at the social layer.
The social layer of a blockchain are all the users, investors, core developers, application developers (who build apps and dapps on the network), miners, and full node operators (such as wallets and exchanges).
These players tend to increase in numbers as the demand for the coin rises because this means that the network is more secure and stable to build their businesses or conduct their activities.
As the ecosystem grows at the social layer; and because these are individuals and businesses distributed all over the world, in different cultures, with different languages and beliefs; it becomes increasingly difficult to coordinate a social attack on the network. This is called "the coordination problem.
The coordination problem minimizes the probability that the ecosystem will ever agree on a controversial change of the protocol, thus increases security at the social layer.
2. Security and risks at the physical and social layers.
The physical and social layers described above may be represented as in the diagram below.
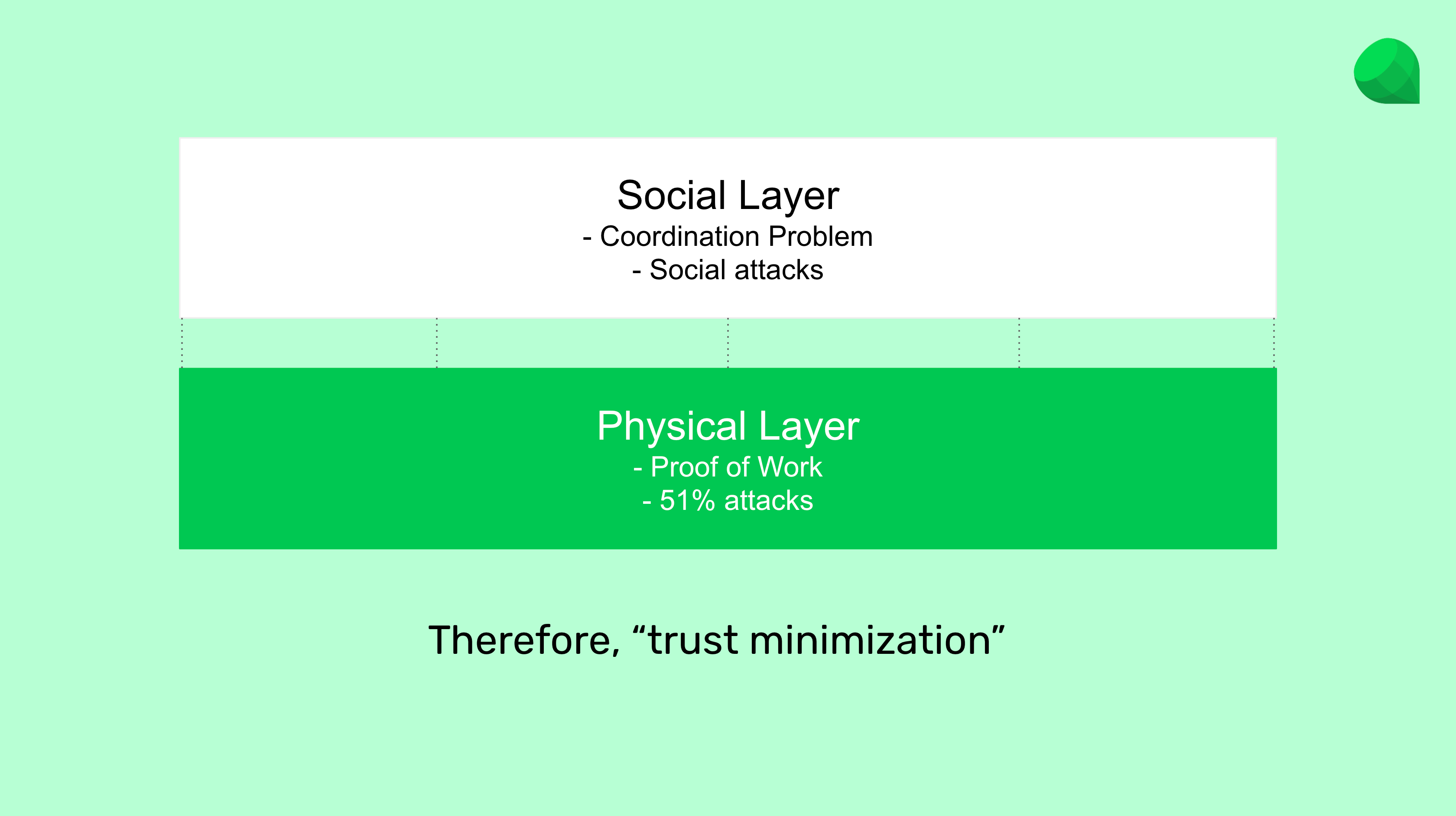
The physical layer is the operating live network, and the social layer are the sum of all individuals and businesses administrating and using the blockchain for various reasons and purposes.
It is important to note that there are risks in blockchains, no matter how secure they are and how these risks are minimized.
2.1. Risks at the physical layer.
The first risk is at the physical layer and it is called a "51% attack". This kind of attack can only be performed if someone has 50% or more of the computing power of a proof of work blockchain. It consists of stealing money from another user by sending them money and then producing an alternative block where the transaction is deleted, therefore pulling back the money sent.
Of course, this risk is reduced significantly when blockchains grow to the size of Bitcoin and Ethereum 1.0 today, but is possible nonetheless.
2.2. Risks at the social layer.
The second risk is at the social layer. It is possible that all the individuals and businesses operating and using a proof of work blockchain globally could coordinate to introduce a controversial change or even confiscate or delete accounts, balances, or smart contracts.
However, as the planetary ecosystem grows, it becomes increasingly difficult to coordinate this kind of activity, especially when it is disagreeable to the majority. Not only that, but blockchains may be forked and continue as before, even if malicious changes are introduced to a new version of the protocol.
3. The concept of trust minimization.
All of the above goes to demystify the concept of "trustlessness". The truth is that proof of work blockchains are not "trustless", they are "trust minimized". This is because the marginal risks explained above still exist.
But, because these are known and transparent threats to a proof of work blockchain, albeit unlikely, it is possible to take measures at the individual and business level to increase the safety of use of these networks.
For example, to use more confirmations when receiving cryptocurrency from untrusted parties, or making sure to support or not support and use any fork of a blockchain that does not provide the guarantees of decentralization.
Thank you for following this class!
Please download and start using Emerald here: