Emerald Blockchain Course class 12 about Proof of Authority.
You can watch this class here:
In the following sections we will explain what is the Proof of Authority (PoA) consensus mechanism, how it works, and its benefits and drawbacks.
1. Trusted block producers.
Proof of Authority is another consensus mechanism such as Proof of Work or Proof of Stake, but instead of using miners or stakers it uses chosen trusted block producers, also known as validators.
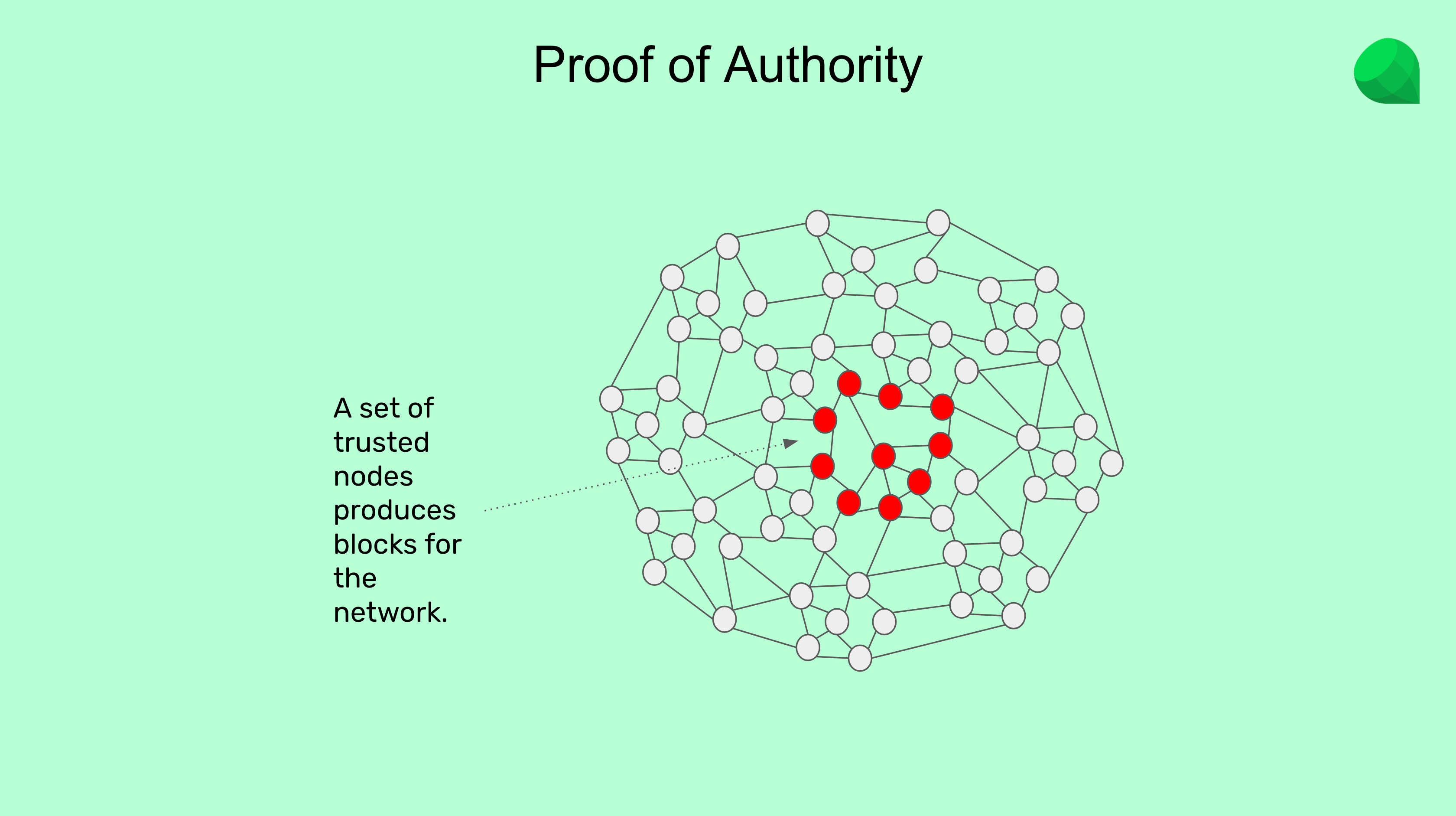
PoA validators do not spend large amounts of electricity or deposit large amounts of capital to have the privilege of producing blocks and receiving the block rewards. The assumption in this type of network is that because they are respected and reputable entities, then they will be honest.
2. How does Proof of Authority work?
The consensus mechanism to reach agreement on which is the next block in a PoA network is very similar to Proof of Stake, but where the validators do not actually have a stake in the network:
1. One of the trusted validators is randomly chosen per round to produce a block.
2. Then it sends the block to the rest of the trusted validators.
3. The rest of the trusted validators vote by two thirds or unanimous majority to approve the block.
4. The block is then included in the database or “blockchain” by the rest of the network.
5. A reward is paid to the trusted validator who produced the block.
The above model has a fault tolerance of 1/3rd. This means that if one third of the validators decide to be dishonest, then they may disrupt the network.
3. Benefits and drawbacks.
Benefits: Similar to Proof of Stake, as validators are known and are few, they can produce blocks more frequently and the blocks may be bigger so this makes Proof of Authority networks more scalable.
Drawbacks: As there are fewer validators and they are trusted, this makes these systems more centralized.
In general terms, one could say that among all the consensus mechanisms and traditional systems, the following would be a ranking of security as measured by centralization:
1. Most secure: Proof of Work
2. Less secure: Proof of Stake
3. Even less secure: Proof of Authority
4. Most insecure: Traditional centralized systems
Thank you for following this class!
Please download and start using Emerald here: